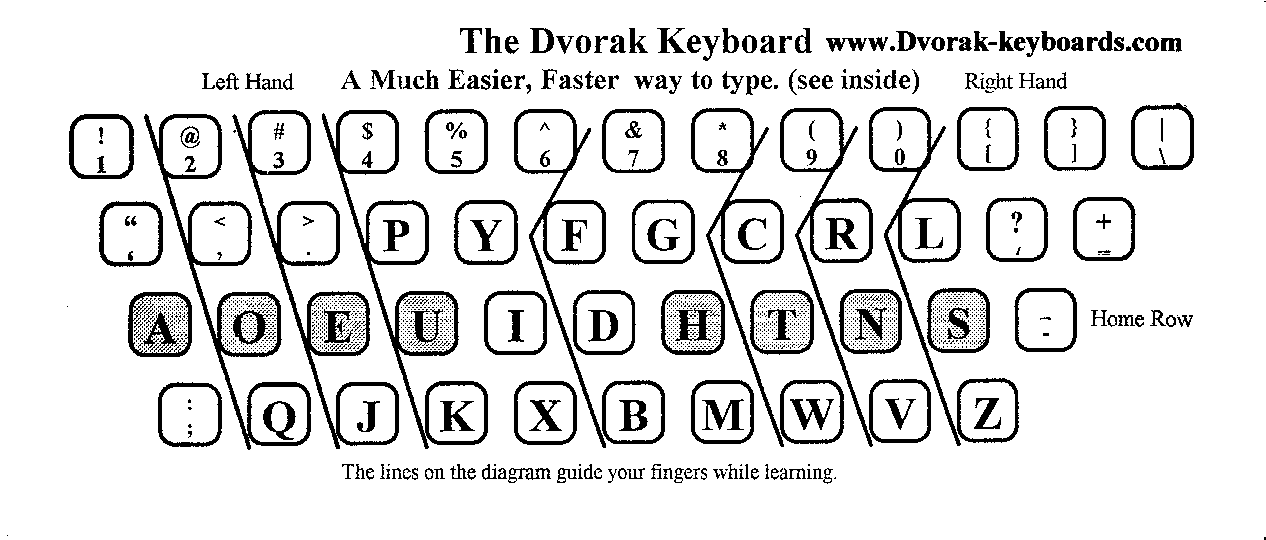
Although the QWERTY keyboard is the most commonly used keyboard format, a second keyboard with emerging popularity also exists called the Dvorak keyboard. This keyboard has all the numbers in the same place as the QWERTY keyboard but all the letters have been rearranged. Users of the Dvorak keyboard claim that if time and devotion are put towards learning how to use the Dvorak format, a user can adapt to the new format in about a month.
It is easier said than done to switch to the Dvorak format, however. Since nearly all computers still use qwerty format, it is difficult for a user to practice using only the Dvorak format since most people will have to use non-personal computers through out their week which will disrupt Dvorak practice. But for those that are passionate enough to try and learn the new format there are lessons and tutors who are willing to help anyone who desires to switch from qwerty to Dvorak.